Cybersecurity Risk Assessment
Cybersecurity risk assessment plays a crucial role in safeguarding digital assets against potential threats and vulnerabilities. As an expert in the field, I understand the importance of conducting regular assessments to identify and mitigate risks effectively. By evaluating various aspects of an organization’s IT infrastructure, from network security to data protection measures, I can pinpoint weaknesses that could be exploited by cyber attackers.
One key aspect of cybersecurity risk assessment is staying updated on the latest threat intelligence trends and attack vectors. This allows me to proactively assess potential risks before they materialize into actual breaches. Leveraging cutting-edge tools and methodologies, I can provide comprehensive risk assessments that help organizations stay one step ahead of cyber threats.

Understanding Cybersecurity Risk Assessment
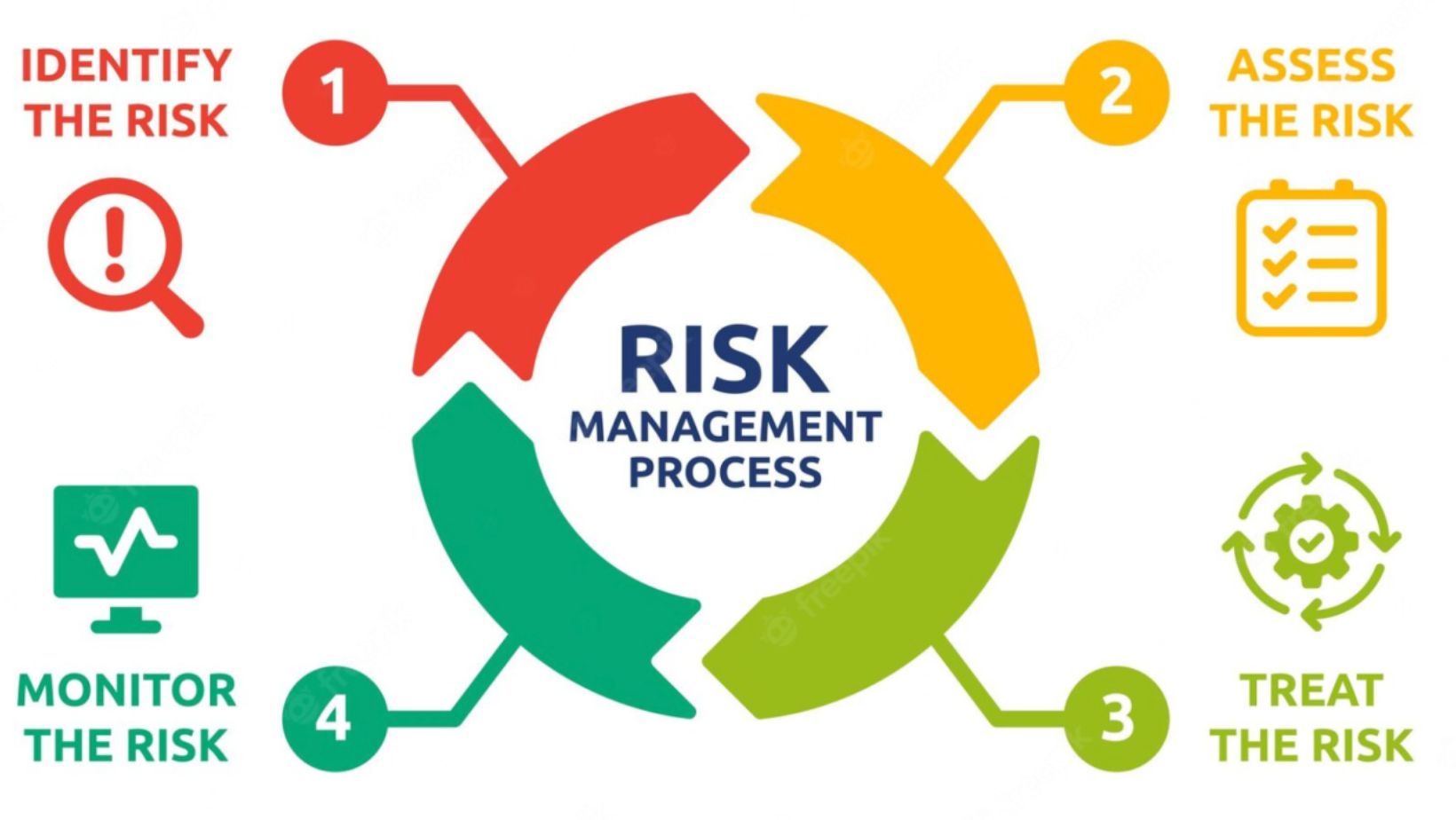
Cybersecurity risk assessment is a crucial process in identifying, analyzing, and evaluating potential risks to an organization’s digital assets. It involves assessing vulnerabilities, threats, and impacts to determine the likelihood of security incidents occurring. By conducting a thorough cybersecurity risk assessment, organizations can proactively address weaknesses in their systems and develop effective strategies to protect against cyber threats.
In today’s interconnected world, where cyber attacks are becoming increasingly sophisticated and prevalent, understanding cybersecurity risk assessment is paramount for businesses of all sizes. It helps organizations prioritize their security efforts based on the level of risk each vulnerability poses. This proactive approach enables companies to allocate resources efficiently and implement mitigation measures that align with their overall business objectives.
One key aspect of cybersecurity risk assessment is the categorization of risks based on their potential impact on the confidentiality, integrity, and availability of data. By classifying risks according to these criteria, organizations can focus on addressing the most critical threats first. This targeted approach empowers businesses to strengthen their defenses where it matters most and minimize the likelihood of significant data breaches or system compromises.
Moreover, cybersecurity risk assessment is not a one-time activity but rather an ongoing process that should be regularly reviewed and updated as new technologies emerge and threat landscapes evolve. Continuous monitoring allows organizations to adapt quickly to changing circumstances and ensure that their security measures remain robust against emerging cyber threats. By integrating risk assessment into their overall cybersecurity strategy, businesses can stay ahead of potential vulnerabilities and safeguard their digital assets effectively.
Importance of Cybersecurity Risk Assessment
Cybersecurity risk assessment plays a VITAL role in safeguarding organizations from potential threats and vulnerabilities. It’s not just about identifying weaknesses; it’s about understanding the IMPACT they can have on operations, data, and reputation. By conducting thorough risk assessments, companies gain valuable insights into their security posture and can PROACTIVELY address issues before they escalate.
Why is Cybersecurity Risk Assessment Important?
- Preventive Measures: A comprehensive risk assessment allows organizations to pinpoint areas of weakness in their IT infrastructure and systems. This insight enables them to implement preventive measures to STRENGTHEN their defenses against cyber attacks.
- Regulatory Compliance: In today’s regulatory environment, compliance with data protection laws such as GDPR and HIPAA is NON-NEGOTIABLE. Conducting regular risk assessments helps ensure that organizations meet these requirements, avoiding hefty fines and legal repercussions.
Benefits of Regular Risk Assessments
- Strategic Decision-Making: Understanding potential risks empowers businesses to make informed decisions regarding cybersecurity investments. By prioritizing identified threats based on likelihood and impact, organizations can allocate resources more effectively.
- Enhanced Incident Response: In the event of a security breach or incident, having a recent risk assessment report at hand can significantly expedite the response process. Teams are better equipped to contain breaches and mitigate damages promptly.


